Cybersecurity in The U.S. in 2023: Cases, Statistics, And Protocols
Introduction
Today, any company, whether large or small, is at significant risk of suffering a data breach or cyber-attack. This is because hackers and cybercriminals constantly implement new tactics to steal confidential information or personal data to sell to third parties or hold the company for ransom.
According to the report conducted by the Identity Theft Resource Center (ITRC), the year 2021 saw a record number of data breaches in the United States. That figure surpassed the previous 1506 set in 2017 and represented a 68% increase over the 1108 breaches recorded in 2020.
The sectors most targeted by this attack are healthcare, finance, business, and retail, affecting millions of citizens in the United States annually As a result, many cybersecurity experts predict that the number will increase in 2023 and beyond.
|
Table of Contents |
Most common types of cyber-attacks
There are thousands of known variants of cyber-attacks; below, we describe the ones that affect companies most frequently.
Ransomware
This attack is one of the most common, and it is generally carried out using extortion techniques, such as threats to expose confidential data if a ransom is not paid. In many of these cases, ransom payment does not provide a solution because no data restoration is achieved.
Malware
There is a wide variety of malware, and ransomware is just one of them. Malicious programs are often used to achieve various goals, from stealing information, defacement, altering web content, or permanent data to the computer system. The evolution of malware is advancing rapidly, but the most common are the following:
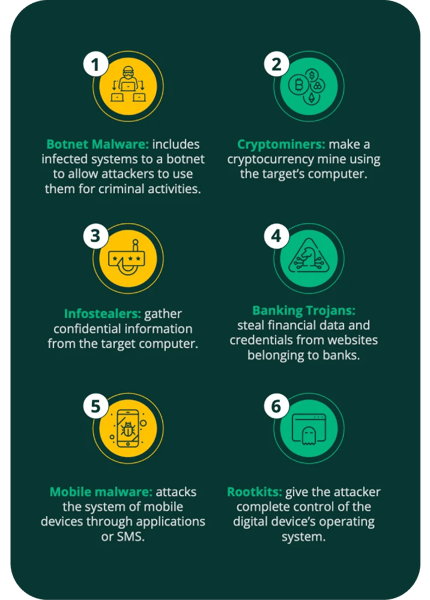
DoS and DDoS attacks
Denial-of-service (DoS) attacks are responsible for saturating a system so that it does not respond correctly to requests, and distributed denial-of-service (DDoS) attacks involve multiple machines.
In both cases, the target site is saturated with illegitimate service requests and is forced to deny access to legitimate users. This is because the servers use all available resources to respond to the overload of submissions.
These attacks do not give the attacker access to the target system and do not directly benefit the attacker. They are only used to sabotage or distract the security team while other attacks are being carried out.
Using firewalls and network security solutions can effectively protect against DoS attacks on a small scale. For protection against large-scale DDoS attacks, enterprises require cloud-supported DDoS resiliency, which can be scaled up on demand to respond to many malicious requests.
Phishing and social engineering attacks
Social engineering is an attack vector supported primarily by human interaction, used in approximately 90% of cyber-attacks. In this attack, an individual impersonates a trusted person or entity to trick people into providing confidential information, transferring funds, and allowing access to the organization's systems.
Phishing occurs when an attacker obtains essential information from a target and sends a message that appears to come from a legitimate and trusted source. The term "phishing" refers to the attackers somehow being dedicated to "fishing" for relevant information, taking advantage of the unsuspecting user to trick them with an emotional hook and a trusted identity.
In addition, attackers, when phishing, usually send links to malicious websites to encourage the user to download malicious software or seek important information via email, text messages, or social networks.
MitM attacks
Man-in-the-Middle (MitM) is an attack that establishes breaches that enable attackers to intercept data transmitted between networks, computers, or users. In this attack, the attacker positions himself between the two parties to eavesdrop on their communication, avoiding detection.
In addition, the attacker can edit the messages before sending them to the recipients. In the face of MitM attacks, the best way to protect yourself is to use VPN or encryption to access the access points.
Fileless attacks
Fileless attacks are malware that intervenes in applications installed on users' mobile devices, which are considered secure. Unlike traditional malware, fileless attacks must be deployed on a target machine, so antivirus tools cannot detect them.
This type of attack can be originated from user-initiated actions, but they can also be triggered without user action, exploiting vulnerabilities within the operating system.
Fileless malware establishes itself in the device's RAM. It accesses native tools that are part of the operating system, such as PowerShell and Windows Management Instrumentation (WMI), to incorporate malicious code.
The 5 most shocking cyber-attacks in the U.S.
Cyber-attacks are malicious actions of access and vulnerability against an organization's IT infrastructure; their high incidence in the last decade has led them to position themselves as the fifth most significant risk for institutions. According to the World Economic Forum report, their incidence is expected to double by 2025.
This latent risk that cyber-attacks represent in the current scenario for institutions and especially for growing enterprises predicts an annual loss of close to 10.5 billion dollars after the theft, misuse, and destruction of data worsened as of 2020 as a consequence of the COVID-19 pandemic.
To put into context the magnitude of the incidence of these crimes, the risk they pose to any organization in the public or private sector, and the losses they entail, Piranirisk examines one by one the five most shocking cyber-attacks of all time in the United States.
Case 1: Amazon DDoS Attack
Amazon Web Services (AWS) 2020 was the victim of a large-scale distributed denial of service (DDoS) attack. But, the company could stop the reported DDoS attack with a unit transfer rate of 2.3 Tbps (terabits per second), a packet forwarding rate of 293.1 Mpps, and a request per second (RPS) rate of 694,201. Because of these figures, it is considered one of the most significant DDoS attacks in U.S. history.
Case 2: Microsoft Exchange Remote Code Execution Attack
Microsoft Exchange 2019 was the victim of a large-scale attack by a well-known enterprise email server. In this case, the attacker took advantage of the four vulnerabilities they found within Microsoft Exchange servers.
These vulnerabilities made it possible for the attackers to spoof a URL to gain access to an Exchange Server system and gain a storage path on the server to deploy the malware. This remote code execution (RCE) attack allowed the attackers to ultimately compromise the server and thus gain access to all the data.
In this way, the attackers managed to steal confidential information from the affected company's servers by injecting ransomware and then professionally deploying the backdoors, making it almost impossible to trace.
These attacks were far-reaching, as in the United States alone, they affected nine government agencies and more than 60,000 private sector companies.
Case 3: Adobe data breach
In 2013 Adobe, the giant software creator, suffered a cyber-attack that compromised the passwords of almost 40 million accounts. The scope of this attack is not only to force access to the usernames and passwords of its customers, which initially estimated the number of affected people to be close to 3 million.
On the contrary, according to a BBC report, the hackers managed to access and steal a large part of the source code of its famous image editing program Adobe Photoshop, one of the company's most essential products. In addition, the criminals also managed to illicitly access Adobe PDF and ColdFusion web source codes illicitly, putting the company's continuity at risk.
Case 4: Uber's improper access to confidential data
The Uber data breach case that occurred in 2016 was one of the most controversial, not only because of the impact it had, as it affected more than 57 million people, including customers and drivers, but also because the CEO of the famous rideshare platform Travis Kalanick, had knowledge of it but would have kept secret from the authorities, so he was dismissed shortly after.
In this case, the hackers used login credentials to access the platform's private source code repository GitHub, which allowed them to obtain and steal a significant amount of personal data.
Case 5: First American Financial Corp.
One of the most shocking cases of cyber-attacks in American history occurred in 2019 after the massive data leak suffered by First American Financial Corp. under poor data handling policies and practices, which guaranteed neither the privacy nor the confidentiality of its customers' data, were exposed online and that according to Brian Krebs reported more than 885 million confidential files.
This giant, dedicated to offering title insurance and multiple settlement services in the real estate and mortgage sector, suffered at the expense of vulnerabilities present in the design of its Insecure Direct Object Reference (IDOR) website. According to Krebs, this left private information in its database exposed to third parties, as it did not have adequate authentication or verification processes.
Not a hacking case!
According to a report in Forbes magazine, this was not a case of hacking because there was no forced access to its database or violation of the servers, but rather errors in handling the information that quickly put it in the wrong hands.
First American used an EaglePro application to store customer information, property information, policy payments, and escrow deposits. But it created links on its website that contained all this private information, so only a specific part of the visitors could access it.
The main problem was that anyone accessing a specific URL of firstam.com could see the data and records of all customers without needing a password; they just had to know where to look.
Effective cybersecurity policies for businesses
According to an IBM report business cost of data leakage in the United States for the past 2022 was about $9.44 million; this amount reveals the need for organizations to implement and constantly update cybersecurity practices for proper information management.
So far, the omissive behavior of organizations, by ignoring this problem, has become a fertile ground for cyber-attacks, which have generated total losses in the United States double the global average. It has led to severe consequences such as financial losses, low productivity, reputational damage, legal liability, and problems in continuing operations.
The government requires organizations to implement multi-factor authentication methods and set up cybersecurity audits to verify their internal systems' healthy functioning continuously.
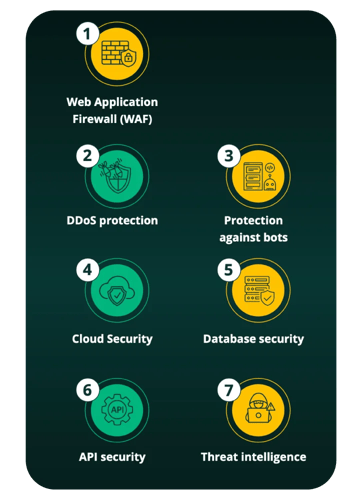
7 Ways to prevent cyber-attacks: Proven solutions
Relevance of cybersecurity audits
Cybersecurity audits consist of a deep analysis of IT practices to detect flaws or vulnerabilities in digital infrastructure. It provides a detailed report that allows the organization to eliminate any errors that hackers can exploit and keep their systems up to date with security protocols.
How is a cybersecurity audit performed?
Companies can perform an internal audit or rely on external providers; in both cases, it evaluates the configuration and operation of your software to identify any gaps that allow data leakage and offer solutions to strengthen security and reduce the risks of cyber-attacks. It is recommended to do this at least once a year.
Piranirisk’s takeaway
1. Frequent software updates
Keeping up to date with the latest version of their software helps companies stay current with security protocols, include new features, fix bugs, and mitigate the risk of vulnerabilities in their security.
2. Train your staff
It is a critical factor that prevents team members from opening suspicious emails or pop-ups that put them at risk of suffering a cyberattack, such as phishing, providing access to source code, or containing malicious files that contaminate systems, as occurred in the cases we analyzed.
3. Use a secure method for sharing data
It is common for any organization to share different files for good communication and collaboration between teams and adopt a solution that prevents interception of information or unauthorized access to information.
4. Install an antivirus
Reduce the risks of online vulnerability by installing a good antivirus and anti-malware software on all the organization's devices.
5. Set up secure passwords
Your team members must be creative and take the time and dedication to create strong passwords, reduce the risk of password theft or forced access.
6. Implement two-factor authentication
Setting up two layers of verification in your security systems allows for much more secure access to organizational accounts by helping to confirm twice that the person logging in is a staff member or customer.
7. Avoid using public networks
We recommend that organizations use private connections, as transferring files or data over public networks exposes them or makes them accessible to other network users. In those cases where a public network is the only option, we suggest using VPN to encrypt the connection and keep it private even for your Internet provider.
Final thoughts
With an incidence of nearly 2,200 cyber-attacks per day, they are undoubtedly a constant risk to the growth and productivity of any organization. However, in Piranirisk, we know that with the use of the right technological solutions, the care in the appropriate cybersecurity protocols, staff training, and customized alert notifications to detect and prevent any vulnerability or malicious action, it is possible to reduce this risk of loss. In a hyperconnected world, companies can keep functioning if they understand the relevance of cybersecurity and the need to be prepared for any crisis and thus focus on efficient management of their business.
Bibliographic references
- https://www.idtheftcenter.org/post/identity-theft-resource-center-2021-annual-data-breach-report-sets-new-record-for-number-of-compromises/
- https://www.upguard.com/blog/cost-of-data-breach
- https://cybersecurityventures.com/hackerpocalypse-cybercrime-report-2016/
- https://www.imperva.com/learn/data-security/data-breach/
- https://www.bloomberg.com/press-releases/2021-02-24/78-lack-confidence-in-their-company-s-cybersecurity-posture-prompting-91-to-increase-2021-budgets
- https://aws-shield-tlr.s3.amazonaws.com/2020-Q1_AWS_Shield_TLR.pdf
- https://www.embroker.com/blog/cyber-attack-statistics/
- https://www.globenewswire.com/news-release/2020/11/18/2129432/0/en/Cybercrime-To-Cost-The-World-10-5-Trillion-Annually-By-2025.html#:~:text=Every%20U.S.%20business%20is%20under%20cyberattack&text=18%2C%202020%20
(GLOBE%20NEWSWIRE),%243%20trillion%20USD%20in%202015. - https://www.bbc.com/news/technology-24740873
- https://www.csoonline.com/article/3268035/adobe-s-cso-talks-security-the-2013-breach-and-how-he-sets-priorities.html
- https://www.bloomberg.com/news/articles/2017-11-21/uber-concealed-cyberattack-that-exposed-57-million-people-s-data#xj4y7vzkg
- https://www.nytimes.com/2022/09/15/technology/uber-hacking-breach.html
- https://krebsonsecurity.com/2019/05/first-american-financial-corp-leaked-hundreds-of-millions-of-title-insurance-records/
- https://www.forbes.com/sites/ajdellinger/2019/05/26/understanding-the-first-american-financial-data-leak-how-did-it-happen-and-what-does-it-mean/?sh=9f3c22567f6a
- https://www.upguard.com/blog/biggest-data-breaches-us
- https://www.ibm.com/reports/data-breach
- https://www.bitsight.com/blog/cybersecurity-audit-assessment-which-do-you-need#:~:text=A%20cybersecurity%20audit%20is%20used,that%20compliance%20requirements%20are%20met.


