Money Laundering and Terrorism Financing Prevention Manual
Introduction
The following money laundering and terrorism financing prevention manual will teach you the main definitions, features and methods to prevent your business from being used for these purposes.
What is money laundering and terrorism financing?
Money laundering is a process in which different economic, financial and commercial transactions are carried out for the purpose of making illicit funds appear legitimate.
Terrorism financing, on the other hand, consists of seeking funds, whether licit or not, to facilitate the perpetration of terrorist actions.
Although the two phenomena are similar, there are several differences between money laundering and terrorism financing, from their motivation and intent to their source of financing and life cycle, as summarized in the table below:
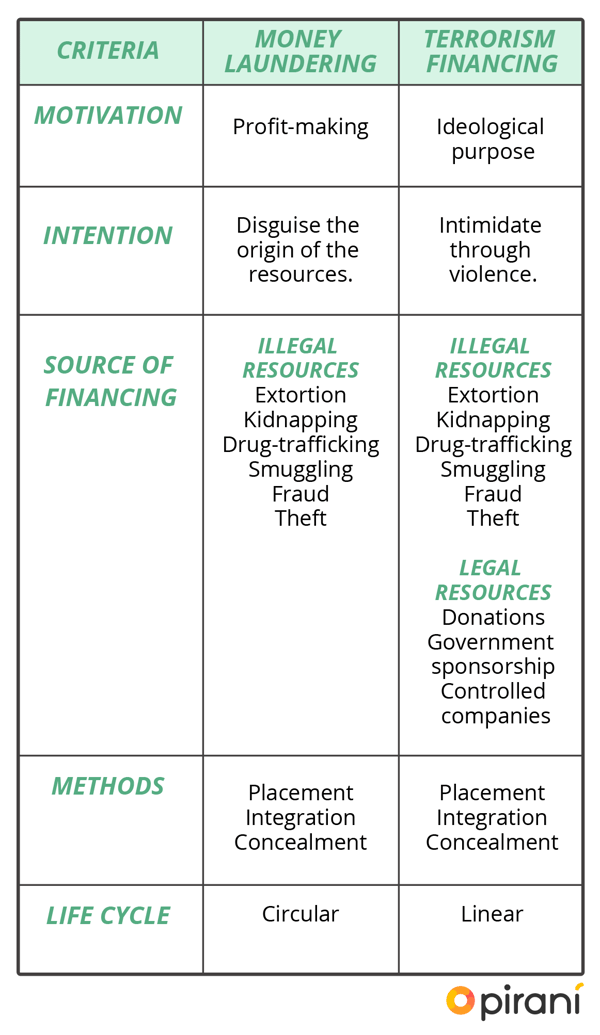
Stages of money laundering and terrorism financing
Through different mechanisms, criminals conceal and integrate funds in the financial system to protect the identity of beneficiaries or benefactors.
The purpose of the money laundering and terrorism financing stages is to conceal the ties between earnings and their sources and to be able to use such money in the formal economy.
1. Stage one: placement
In this phase, criminals introduce the assets they obtain illegally in the financial system. To achieve this goal, they use money exchange offices, fund deposits, front companies, etc.
2. Stage two: concealment
Once the money enters the formal economy, criminals mobilize funds through different transactions in order to complicate the documentary tracking of assets. They change the location of money, modify its origin, transform its nature and place it in another destination.
3. Stage three: integration
However, introducing and concealing the destination of illegitimate assets is not enough. The funds need to be reincorporated in the financial system. At this stage, criminals carry out various economic transactions such as investment in real estate, securities, commercial projects or even trusts. These transactions further overshadow the origin of the money and allow it to circulate legitimately.
Money laundering and terrorism financing risks
The risk of money laundering and terrorist financing consists of the possibility of loss or damage suffered by a regulated organization because of its likelihood to be used as an instrument to launder assets or as a channel of funds to promote terrorist activities.
The risks of money laundering and terrorism financing can destabilize an organization and even push it to the brink if appropriate controls are not carried out.
There are various risks to which an entity is exposed if it does not have a structured plan to prevent money laundering and terrorism financing. These are some of the main risks:
Reputational Risk
When a company is convicted or is under investigation for money laundering, there are certain negative effects on the overall image of the company. This, in turn, lessens the confidence of investors, customers and suppliers, which winds up seriously affecting the entity's economy.
Legal Risk
Preventing money laundering and terrorism financing is not an option for organizations. Since they are criminal offenses, it is mandatory for all companies to avoid being used for that purpose. Therefore, when controlling bodies discover that this is happening, they can impose fines or sanctions with quite serious economic, administrative and judicial implications for a company.
Risk of Contagion
When a company has commercial or other ties with an entity involved in money laundering or terrorism financing, it can suffer reputational damage as for its image. As we explained earlier, this type of risk can cause major economic losses due to the damage done to the trust and good name of the organization.
Although no company is exempt from being used to launder money or finance terrorism, there are certain types of companies, industries or economic sectors that are more likely to be used for such purposes. These include corporations, foundations or non-profit entities, as well as politically exposed persons (PEPs) and entities engaged in high-risk economic operations.
There are also some high-risk businesses, such as exchange offices, transfer offices, check-cashing businesses, casinos and online gaming.
In addition to the risks of money laundering and terrorism financing that we have already mentioned, these crimes have consequences that affect both the organizations involved and society as a whole:
- They enable drug traffickers, terrorists, illegal arms dealers or corrupt public officials to continue carrying out their illicit activities.
- Money launderers gain a competitive advantage that does not allow legitimate businesses to compete in equal conditions with those who mix illicit funds with legitimate financing.
- They cause liquidity problems in financial institutions due to the entry and withdrawal of large amounts of money.
- They generate sudden changes in money demand, destabilize the flows of international capital, interest rates and exchange rates.
- Tax revenues are reduced, which affects taxpayers. This forces raises in taxes to fill the tax gap.
- They affect the country's financial system and reputation.
Most common money laundering strategies
Organized crime often optimizes its tactics to transform the true source of its income.
In the past, the mafia bought automatic laundries to "legalize" the money they were making with their illegal activities. Today criminals have refined their tactics much further. At present, they use the securities market as a tool to legitimize assets from illicit origins.
Along with the advance of technology and the globalization of markets, organized crime has found different ways to launder money.
- Currency smuggling.
- Acquisition of negotiable instruments.
- Smuggling of goods.
- Purchase and sale of goods abroad.
- Investments in insurance companies.
- Use of tax havens.
- Shell companies.
- Currency exchange.
- Purchase of shares and securities on the securities exchange.
- Forged invoices.
- Game and entertainment centers.
- Gambling.
- Clandestine banking systems.
- Purchase and sale of luxury goods.
- Real estate.
- Services trade.
It is also common for money launderers to involve prestigious professionals to earn high incomes through the provision of services. Medicine, engineering, architecture, accounting and law are fairly common forms of front men operations. They also use low-profile individuals to make investments on their behalf and then transfer the deed of the properties.
Methods for preventing money laundering and terrorism financing
In this money laundering and terrorism financing prevention manual, we are providing good practices that you should take into account.
Customer registration
This is done to identify customers' risk category and to facilitate the process of recognizing each of them.
Customer registration is carried out based on a classification of the type of person with the greatest risk of money laundering and terrorism financing: politically exposed persons and suspicious persons, such as those linked to the tourism sector, gaming, air transport, insurance companies, money exchange offices, distributors, etc.
KYC (Know Your Customer)
What is Know Your Customer? It is a process that consists of a series of steps to profile clients and define their activities and sources of funding.
KYC involves double identification. First, documentary recognition is carried out by requesting a copy of the citizen identification, ID card or passport. Then, the purpose for which the customer wants to do business with the entity is established. This means ascertaining the type of professional activity they carry out, the origin of their funds is and what they need the credit, savings or financing for.
The main objective of KYC or know your customer is to know for sure what the customer's behavior is and identify potential suspicious transactions. Preventing money laundering by knowing your customer warns financial entities not to have business relations with organized crime.
How is the Know Your Customer process carried out?
The KYC or know your customer process is a due diligence that investigates the details of the customer's personal and professional life. This process is performed by the compliance area before opening the account or initiating any business relations.
Normally, the customer's workplace, the work site or his/her commercial premises are visited.
There is certain information that must be taken into account when filling out a know your customer form: identity, financial situation, professional activity, payment capacity, personal and professional references and financial institutions with which they have been engaged, among other aspects.
Since the customer's financial situation can change at any time, know your customer information must be permanently updated.
Implementing a digital technology tool to facilitate the process is a good practice to prevent money laundering and terrorism financing. Automating the process allows the compliance and risk management areas to answer key questions, update information quickly, and identify warning signs in real time.
Monitoring unusual or suspicious transactions
Financial entities must have an internal control system, a set of measures to control the operation of their activities and their customers. The compliance area is responsible for detecting any operations that indicate possible money laundering.
As broad knowledge of a customer's transactions becomes available, it can better be established whether their movements match the banking history and, in that sense, take timely action.
An effective money laundering prevention system should indicate whether the customer is a politically exposed person, whether there was any alteration in the account data or whether the customer has any business activity at border crossings.
There are several tools for monitoring unusual transactions: through manual monitoring in which a report is created to control transactions, through a computer system that finds inconsistencies in the customer's transactions or by consulting the available lists of suspicious names.
Even now, the possibility of using artificial intelligence as an ally to prevent money laundering and terrorism financing is being explored. With machine learning and big data techniques, we aim to analyze a large volume of information about the customer in order to determine his/her profile and get to know him/her in depth.
Identification of unusual or suspicious transactions
To identify unusual transactions, it is important to recognize warning signs. In this money laundering and terrorism financing prevention manual, we are providing some of them.
Examples of unusual transactions
- Transactions that do not match the customer's occupation.
- Sudden account movements.
- Infrequent transactions.
- Small transfers to other accounts.
- Unjustified changes in the customer's transaction pattern.
There are also some indications to warn about the user's financial behavior:
- Refusing to provide information.
- Unjustifiably changing account information.
- Bribing officials.
- Having an account without validated data.
Customer segmentation
One of the best practices for managing unusual transactions is customer segmentation. This is a process that aims to divide a group of data into several smaller ones.
Segmentation is very important in preventing money laundering and terrorism financing because it allows us to know the profile of a group of users with common characteristics and be able to compare them with each other.
Segmentation is the first thing to do before monitoring unusual transactions or analyzing customer behavior. Through segmentation, similar traits are determined and the usual characteristics of transactions are detected in order to establish patterns.
When carrying out this process, it is essential to take into account the following variables:
- Customers.
- Products.
- Distribution channels.
- Nature of the transactions.
Classification trees and cluster analysis are some of the most common methods for segmenting. However, it is the available data that will determine the most appropriate methodology for doing so.
Consult this manual whenever you need it and share it with your employees and collaborators. Click below to download the free PDF.

