5 Tips for Effective Information Security Management

In today's digital landscape, effective information security management is essential for businesses of all sizes. With cyber threats becoming increasingly sophisticated, organizations must prioritize safeguarding their sensitive data and maintaining the trust of their customers. But where do you start?
This article will share 5 essential tips to help you enhance your information security management strategy. From implementing strong passwords and encryption protocols to conducting regular vulnerability assessments, these actionable tips will empower you to protect your organization's valuable information assets proactively.
Our brand believes in simplifying complex concepts making them accessible to everyone. That's why we've crafted this guide to be easy to understand and implement, regardless of your technical expertise. By following these best practices, you can minimize the risk of data breaches and demonstrate your organization's commitment to cybersecurity.
Whether a small business owner or an IT professional, this article offers practical advice to strengthen your information security management process. Stay ahead of hackers and ensure your data's confidentiality, integrity, and availability.
The importance of information security management
Effective information security management is crucial in today's interconnected world. Businesses face many threats, including hacking, malware, data breaches, and insider threats. These incidents can have severe consequences, such as financial loss, reputational damage, and legal implications. Therefore, robust information security measures are vital to protect your organization's assets and maintain stakeholder trust.
To effectively manage information security, it is essential to understand the three core principles of the CIA triad - Confidentiality, Integrity, and Availability. Confidentiality ensures that only authorized individuals have access to sensitive information. Integrity ensures that data remains accurate and unaltered. Availability ensures that authorized users have access to information when needed. Organizations can build a strong foundation for their information security management strategy by focusing on these principles.
Common threats to information security
Before delving into the tips for effective information security management, it's crucial to understand the common threats that organizations face. Cybercriminals employ various tactics to breach security defenses and gain unauthorized access to sensitive data. Some of the most prevalent threats include:
Phishing Attacks: Phishing attacks involve tricking individuals into revealing sensitive information by posing as trustworthy entities, such as passwords or credit card details.
- Malware: Malware, including viruses, worms, and ransomware, is designed to infiltrate systems, steal data, or disrupt operations.
- Insider Threats: Insider threats come from within an organization, where employees, contractors, or partners misuse their access privileges or intentionally leak confidential information.
- Social Engineering: Social engineering involves manipulating individuals into revealing sensitive information or performing actions compromising security.
- Distributed Denial of Service (DDoS) Attacks: DDoS attacks overload a system or network with an overwhelming amount of traffic, causing it to become unavailable to legitimate users.
Understanding these threats is essential for developing effective information security management practices and implementing appropriate safeguards.
Understanding the CIA triad - Confidentiality, Integrity, and Availability
Organizations should establish an Information Security Management System (ISMS) to manage information security effectively. An ISMS framework includes policies, processes, and procedures to protect information assets and manage risks. Here are the key steps to establish an ISMS:
- Define the Scope: Identify the boundaries and applicability of the ISMS within your organization, considering factors such as departments, systems, and data.
- Conduct a Risk Assessment: Assess your organization's risks, including potential vulnerabilities and threats. This step helps prioritize security efforts and allocate resources effectively.
- Develop Policies and Procedures: Create comprehensive policies and procedures that outline the organization's information security objectives, responsibilities, and actions to be taken in different scenarios.
- Implement Security Controls: Implement appropriate security controls and safeguards based on the identified risks and organizational requirements. This may include access controls, encryption, firewalls, and intrusion detection systems.
- Monitor and Review: Continuously monitor and review the effectiveness of the implemented security controls and make necessary adjustments to address emerging threats or vulnerabilities.
Implementing an ISMS provides a structured approach to information security management, ensuring security measures are consistent and aligned with the organization's objectives.
Establishing an information security management system (ISMS)
A risk assessment is a critical step in information security management. It helps identify potential vulnerabilities, threats, and the likelihood of their occurrence. Organizations can prioritize security efforts and allocate resources effectively by understanding these risks. Here's a step-by-step guide to conducting a risk assessment:
- Identify Assets: Identify the information assets your organization needs to protect, including customer data, intellectual property, financial information, and systems.
- Assess Threats and Vulnerabilities: Identify potential threats and vulnerabilities that could compromise your information assets' confidentiality, integrity, or availability. This may include external threats, such as hacking, and internal threats, such as employee negligence.
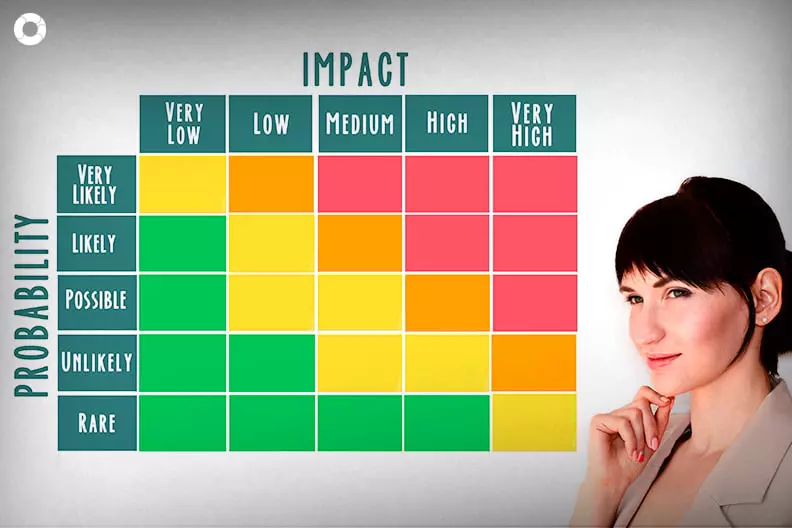
- Evaluate Likelihood and Impact: Assess the likelihood of each identified threat occurring and its potential impact on your organization. This step helps prioritize risks based on their severity.
- Determine Risk Levels: Assign risk levels to each identified threat based on the likelihood and impact. This step helps identify high-risk areas that require immediate attention.
- Implement Controls: Implement appropriate security controls and safeguards to mitigate identified risks. This may include technical controls, such as firewalls and encryption, as well as procedural controls, such as employee training and access restrictions.
By regularly conducting risk assessments, organizations can proactively identify and address potential vulnerabilities, reducing the likelihood of security incidents.
Conducting a risk assessment
Implementing security controls and safeguards is crucial for protecting sensitive information from unauthorized access, disclosure, alteration, or destruction. Here are some essential security controls to consider:
- Strong Passwords: Enforce solid and complex passwords that are difficult to guess. Encourage users to use uppercase and lowercase letters, numbers, and special characters.
- Multi-Factor Authentication (MFA): Implement MFA to add an extra layer of security. MFA requires users to provide additional verification, such as a one-time password or biometric authentication, in addition to a password.
- Encryption: Encrypt sensitive data in transit and at rest to protect it from unauthorized access. Encryption ensures that even if data is intercepted or stolen, it remains unreadable without the encryption key.
- Regular Patching and Updates: Keep software and systems updated with the latest security patches and updates. Cybercriminals can exploit vulnerabilities discovered in software, so timely patching is essential.
- Firewalls and Intrusion Detection Systems: Deploy firewalls and intrusion detection systems to monitor network traffic and detect and block unauthorized access attempts.
- Data Backup and Recovery: Regularly back up critical data and test the restore process to ensure that data can be recovered during a security incident or system failure.
Implementing these security controls and safeguards helps create layers of defense, making it more challenging for attackers to breach your organization's information security.
Implementing security controls and safeguards
In addition to technical measures, training and educating employees on information security best practices is crucial. Employees are often the weakest link in an organization's security posture, as their actions can unintentionally expose sensitive information or fall victim to social engineering attacks. Here are some effective strategies for employee training and education:
- Security Awareness Programs: Develop and implement security awareness programs to educate employees about the importance of information security and common threats they may encounter.
- Phishing Simulations: Conduct regular phishing simulations to test employees' susceptibility to attacks. These simulations help raise awareness and train employees to identify and report phishing attempts.
- Role-Based Training: Provide role-specific training to employees based on their responsibilities and access privileges. This ensures that employees understand their security responsibilities and follow best practices.
- Incident Reporting Procedures: Establish apparent incident reporting procedures to encourage employees to promptly report suspicious activities or incidents.
- Continuous Education: Information security threats and best practices evolve rapidly. Encourage employees to stay updated through continuous education, such as attending security webinars and conferences, or completing relevant certifications.
By investing in employee training and education, organizations can create a security-conscious culture and reduce the likelihood of security incidents caused by human error.
Training and educating employees on information security
Despite the best preventive measures, security incidents may still occur. A well-defined incident response plan minimizes the impact and quickly restores normal operations. Here's an overview of the key components of an incident response plan:
- Incident Identification: Establish processes and tools to detect and identify security incidents promptly. This may include automated monitoring, intrusion detection, or employee reporting mechanisms.
- Incident Response Team: Form an incident response team comprising individuals from different departments, such as IT, legal, and public relations. This team should be responsible for coordinating the response to security incidents.
- Incident Escalation and Communication: Establish clear escalation and communication channels to ensure that the right individuals are notified promptly when a security incident occurs. This includes internal stakeholders, senior management, and external parties, such as law enforcement or regulatory authorities.
- Containment and Eradication: Take immediate action to contain the incident, prevent further damage, and eradicate the root cause of the incident. This may involve isolating affected systems, restoring backups, or applying patches.
- Forensic Analysis and Investigation: Conduct a thorough forensic analysis to determine the extent of the incident, identify the vulnerabilities exploited, and gather evidence for potential legal or disciplinary actions.
- Lessons Learned and Continuous Improvement: After resolving the incident, conduct a post-incident review to identify lessons learned and areas for improvement. Update policies, procedures, and security controls based on these findings.
By having a well-prepared incident response plan, organizations can minimize the impact of security incidents and return to normal operations quickly.
Conclusion: Maintaining a solid information security posture
Pirani enables you to effectively and easily manage the risks associated with information security by being able to manage your organization's information assets. Make action plans and strategic controls to reduce the risk of cyber-attacks that may cause a loss of data or valuable information in your organization.
Reduce time by recording incidents that may affect the security of your organization's information from any mobile device and obtain relevant data for decision-making in case of cyber-attacks or loss of information. Try Pirani for free!
You May Also Like
These Related Stories

5 steps to make a risk map
Prioritize risk with a control matrix

Know the components of the internal control of a company

How can your organization's information be protected in Pirani?

Top 10 Best Information Security Software

No Comments Yet
Let us know what you think