Integrate Pirani into your workflow
Integrate Pirani into your workflow
2:20

Now you will be able to integrate Pirani into your organization's workflow with the new functionalities in the system settings section. In this section you will find the necessary information to perform the integrations and authentications that allow you to incorporate Pirani to your activities.
Remember that these functionalities are available from the Enterprise plan.⚡
These are the functionalities you will find at ⚙️
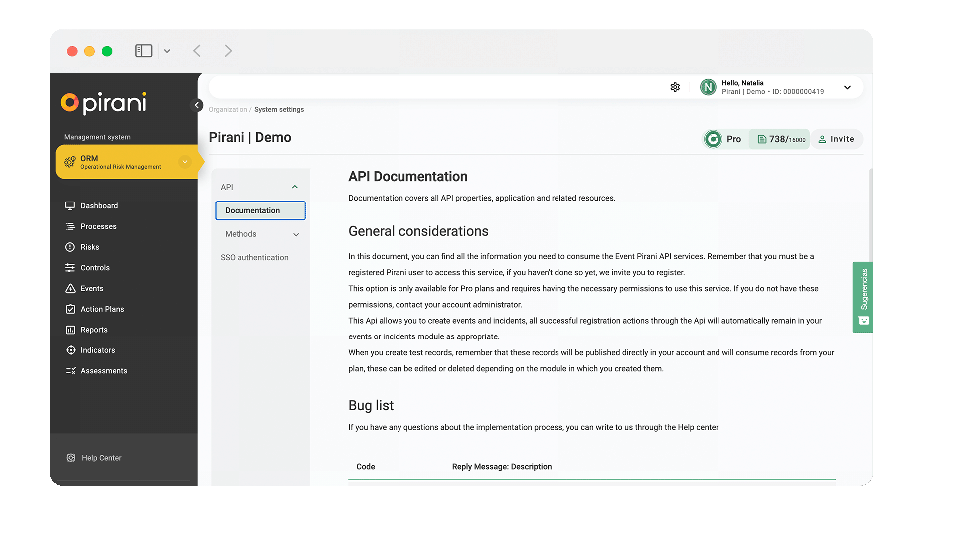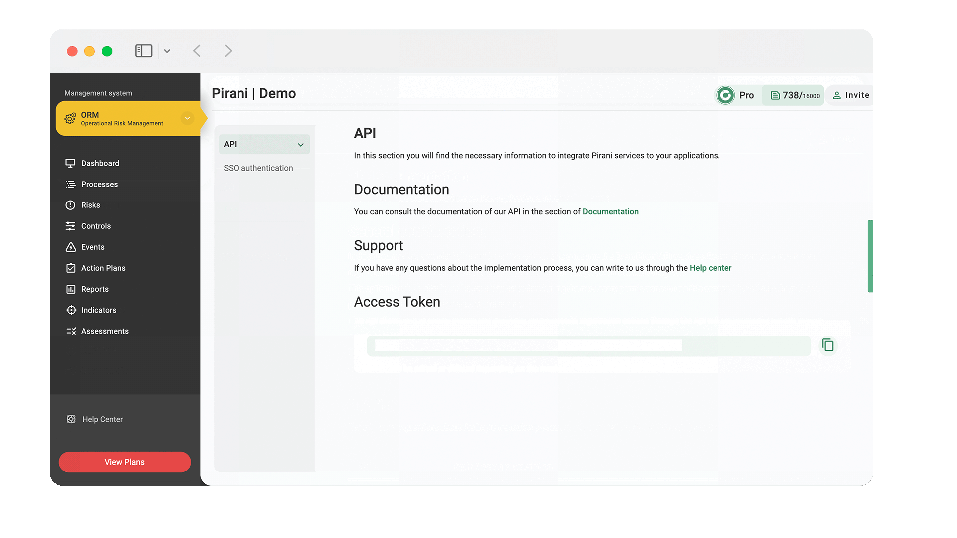
API for event creation
With the new API integration functionality you will be able to transfer to Pirani the events you have registered in your current incident reporting systems and manage them in one place.
Learn more about how to integrate Pirani for the creation of events in this tutorial where I explain this topic in detail → Api for event creation.
Wait...you don't use Pirani yet? 👀
Discover how simple it is to manage Integrate Pirani to your workflow. Try our tool for free and tell me in the comments of the article what you think about the system settings functionalities.
Single Sign-On (SSO)
Now your organization will be able to govern within Pirani the users and login credentials of the work team, by performing the SSO single sign-on configuration. With this configuration you will be able to use your authentication system in Pirani and allow your collaborators to access the tool easily and securely with their SSO credentials.
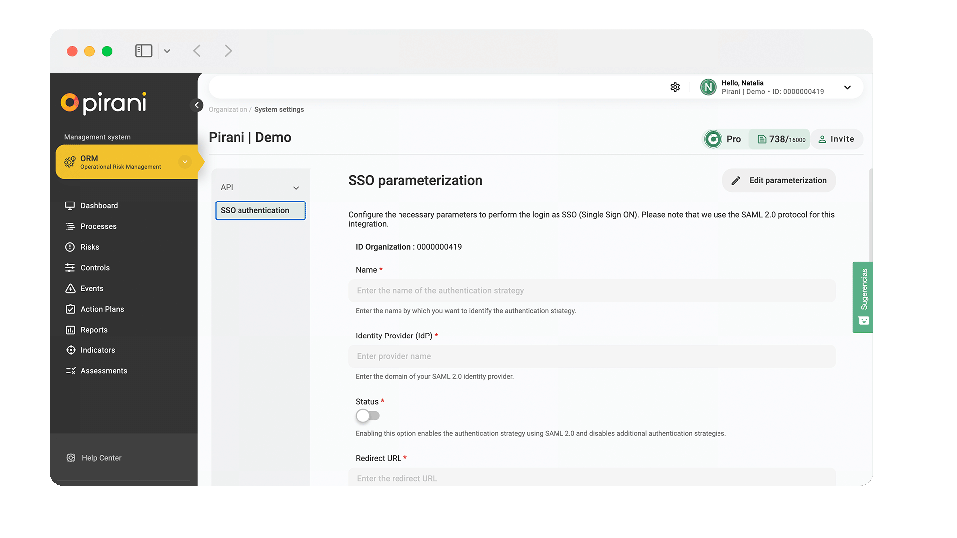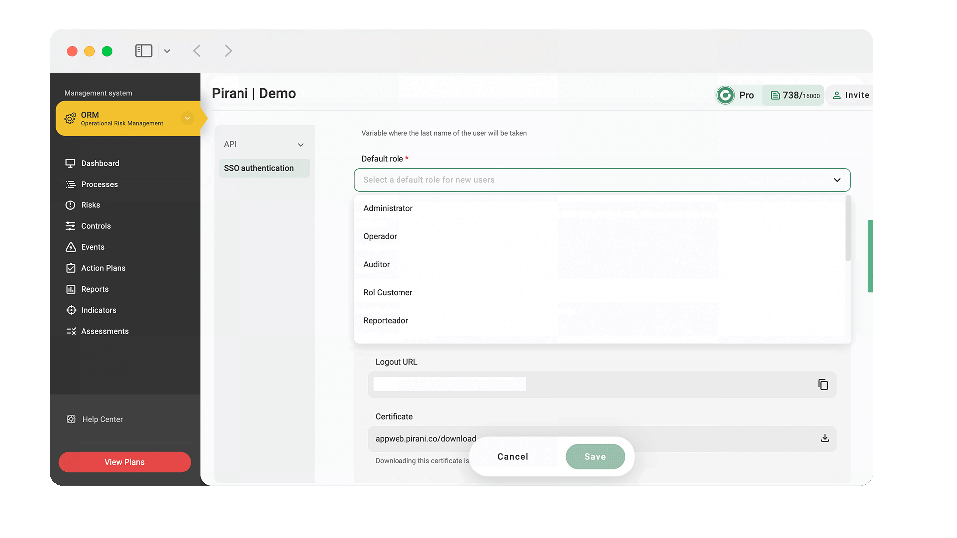
To configure authentication and allow your computer to log in via SSO I leave you this tutorial where I explain in detail this topic → Configure Single Sign-On (SSO).
Multi-Factor Authentication (MFA)
Now your team can add an additional layer of security to their accounts with multi-factor authentication (MFA). This functionality can be configured so that the different types of users that enter your organization through username and password must perform an additional step for authentication. In addition, as administrator you will be able to know who has the authentication enabled or disabled to monitor and comply with the information security policies.
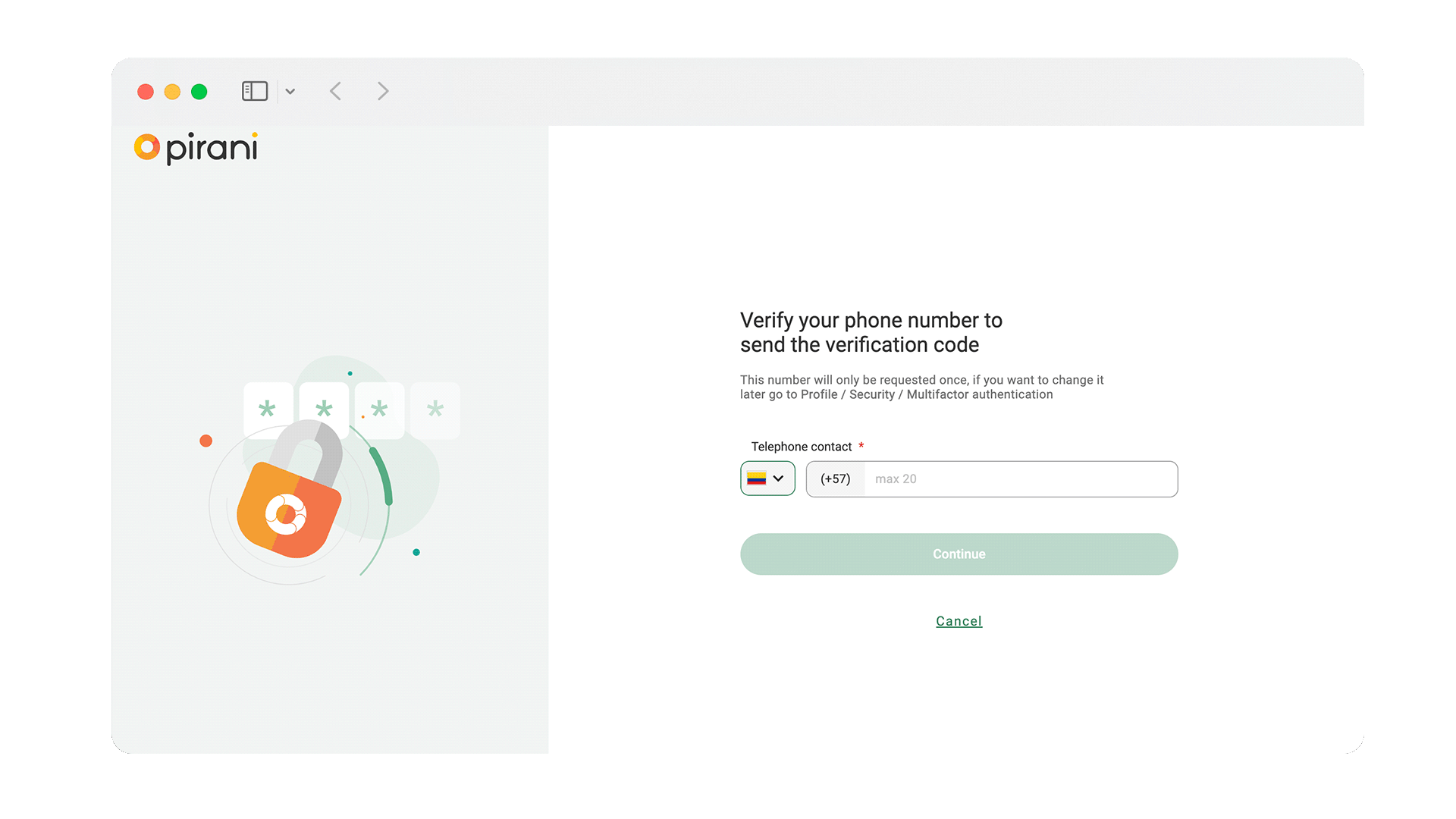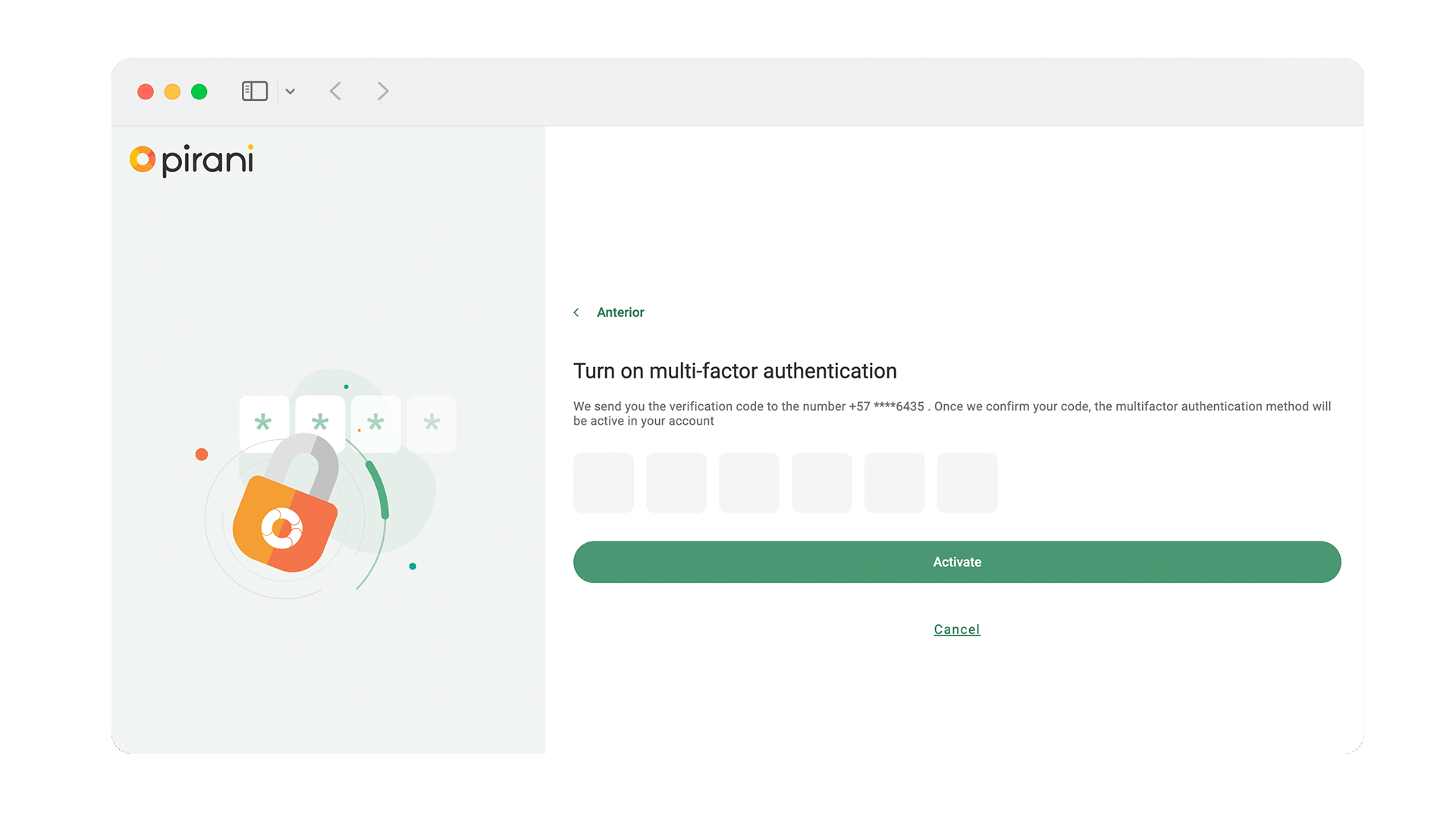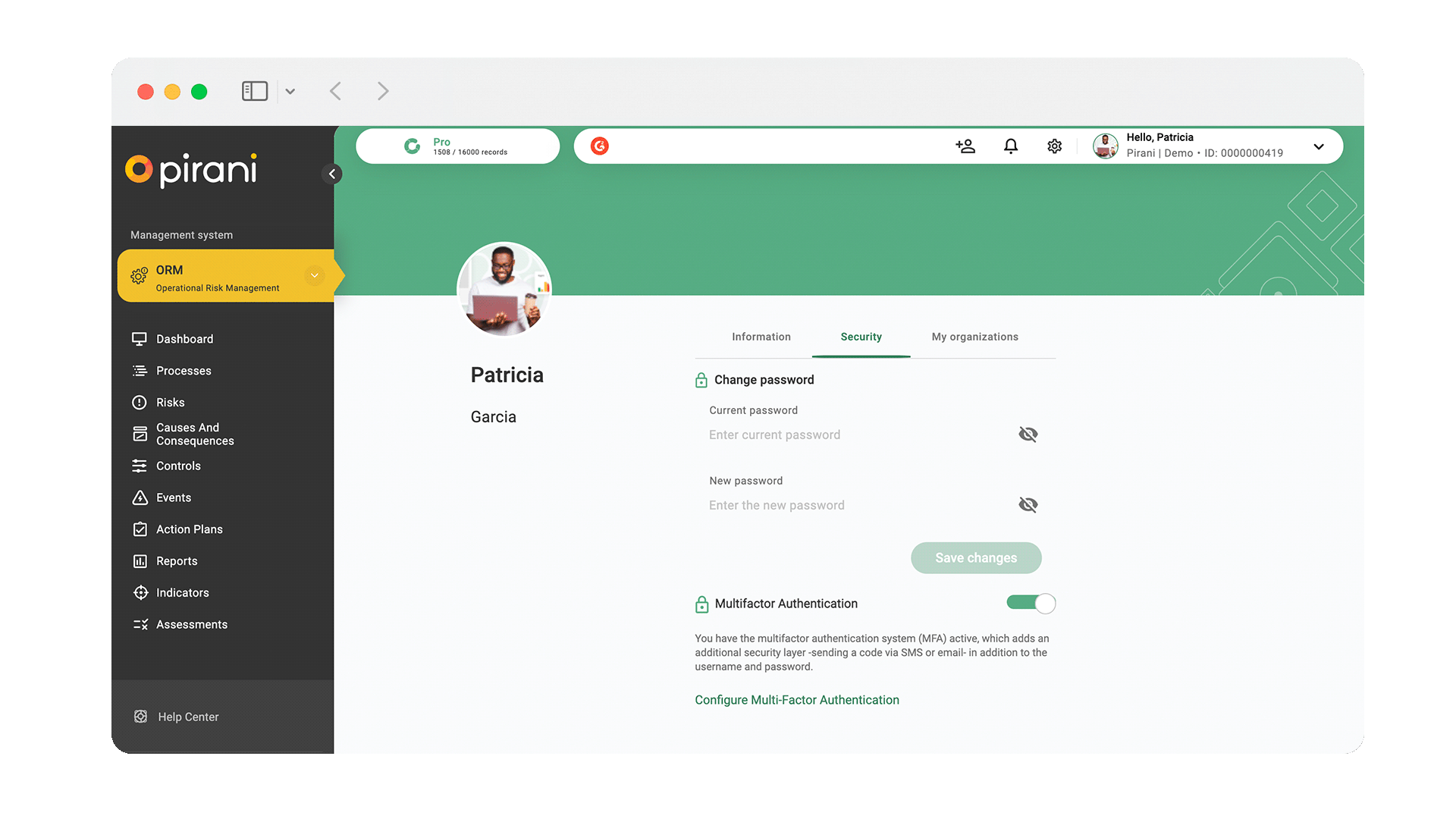
To configure multifactor authentication and allow users to log in with double authentication, I leave you this tutorial where I explain this topic in detail → How does multifactor authentication (MFA) work?
You May Also Like
These Related Stories
How can your organization's information be protected in Pirani?


How can your organization's information be protected in Pirani?
May 16, 2024
3
min read
Successful audits with Pirani


Successful audits with Pirani
August 09, 2023
2
min read
Optimize your processes with bulk imports


Optimize your processes with bulk imports
June 02, 2023
3
min read
You have a new risk management alert! 🔔

You have a new risk management alert! 🔔
March 10, 2023
3
min read
Explore free integral risk management


Explore free integral risk management
December 06, 2023
3
min read
Upgrade your AML risk management with AML+


Upgrade your AML risk management with AML+
April 24, 2023
3
min read


No Comments Yet
Let us know what you think