The 4 key steps to cybersecurity risk management

Cybersecurity is increasingly a topic of concern and interest to organizations of all types of industries and sizes; in fact, according to the Latin America Risk Management Study 2024 that we did in Pirani, the risks associated with this and data protection are the main risks to manage this year for companies in the region. And in the World Economic Forum's Global Risk Report 2024, it ranks fourth for the next two years.
Given this reality and the fact that cyber-attacks continue to increase and are more professional, complex, and sophisticated, it is increasingly necessary to know how to manage these risks properly and effectively in organizations since no organization is exempt from falling victim to cybercriminals.
Below you will learn about the key phases or stages for a good cyber risk management in your organization.
Cybersecurity risk management
Services, computer systems, and, in general, all the information generated, managed, and safeguarded by an organization are susceptible to being affected by a cyber attack. Therefore, the necessary measures and precautions must be taken to protect it as well as possible, and risk management is a strategic process that will help you to do so.
For good cybersecurity risk management, in general, the following key phases or stages should be carried out:
1. Identification of the assets
In this first stage, it is important to make an inventory of the organization's information assets, i.e., all the physical or intangible elements that make up the information structure and that are attractive for attack by cybercriminals. Here, we can consider, for example, assets such as hardware, software, services, internet networks, and people, among others.
And it is key to qualify their criticality taking into account aspects such as: confidentiality (access to information), integrity, availability and traceability. This classification allows to know which are the most critical assets for the organization and represent a higher risk.
2. Identification and evaluation of risks
As a key player in the risk management process, your role in identifying and evaluating the potential risks that could affect our information assets is crucial. After having the inventory of these assets, it's your expertise that will guide us in this important task.
The techniques we use for risk identification are not just arbitrary methods, but proven strategies that have been successful in various organizations. These include interviews with the owners of the processes and assets, scenarios (what if...), and knowledge of what has happened or happens in organizations of the same industry or another one. Your familiarity with these techniques will ensure a comprehensive risk assessment.
Some of the risks to consider are: service interruption, information leakage, system failures, theft of documents and computer equipment, cyber-attacks such as phishing, ransomware or denial of service (DDoS), loss of access control and any other that affects the proper functioning and continuity of the organization.
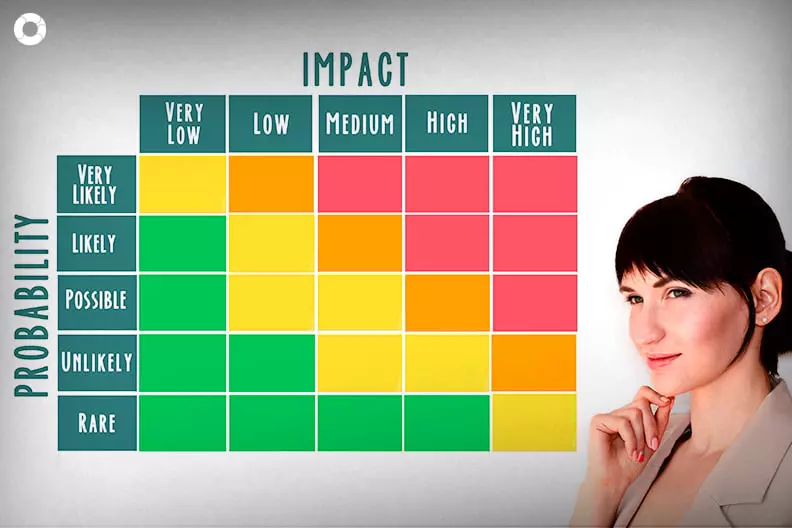
Additionally, at this stage, each of the identified risks must be analyzed and evaluated, i.e., assessed in terms of their probability of occurrence (how likely is it to materialize?) and their impact (consequences that their materialization would have in the operational, financial, legal or reputational sphere).
Both qualitative and quantitative variables are commonly used to assess probability and impact. And knowing the values of these two elements, which results in the inherent risk, serves to prioritize the risks and thus be able to establish the necessary measures to deal with them promptly.

3. Risk treatment
Once the potential risks to which the information assets are exposed have been identified and assessed, it is crucial for us, as information security professionals, risk managers, and organizational decision-makers, to define the treatment measures to be implemented. These measures, which include mitigation, transfer, acceptance, or avoidance of risks, are not just options, but our decisions that significantly impact the security of our information assets.
Mitigation, one of the most effective measures, is widely implemented through controls. These controls, whether preventive, detective, or corrective, can be executed automatically, manually, or in combination. They not only reduce the probability of occurrence of the risk but also minimize the impact caused if it materializes. This effectiveness should give us confidence in our ability to protect our information assets.
Annex A of ISO 27001:2022 includes a total of 93 controls, organized in four sections (organizational, physical, technological and people), for information security risk management. Some of these controls are: physical security monitoring, configuration management, data masking, data leakage prevention, web filtering, employee training, among others.
With respect to the other risk treatment options, the transfer generally involves the purchase of insurance; in this case, it would be cyber risk insurance. Acceptance of risk means recognizing that it exists and deciding to live with it, considering the appetite and tolerance established by the organization. And finally, risk avoidance means ceasing to carry out the activities that generate the risk.
4. Constant monitoring and review
Cybersecurity risk management must be a continuous process, therefore, in this fourth stage a periodic follow-up of the identified risks and the implemented controls must be carried out.
The monitoring of risks serves to know if the same risks are maintained or if there are new risks that need to be included in the management. And in the case of controls, they are followed up to evaluate their effectiveness and to know if they are fulfilling the objective for which they were created or, on the contrary, it is necessary to make adjustments or implement new ones to prevent or mitigate the cyber threats and risks to which the company is exposed every day.
In addition to these four phases or key stages for cybersecurity risk management, it is essential to communicate and raise awareness of these risks to all stakeholders of the organization, as well as the measures and good practices to be implemented to prevent their materialization as far as possible.
Among others, it is important to raise awareness about: using strong and secure passwords, making frequent backup copies, not sharing company information with anyone, making good use of the information to which you have access and reporting any eventuality and suspicious activity in a timely manner.
Manage cybersecurity risks with Pirani
Did you know that through Pirani's information security management system, we can help your organization manage these risks in a simple way?
With Pirani ISMS, you will be able to:
- Identify information assets and qualify them in their criticality.
- Identify and evaluate cybersecurity risks.
- Identify and manage threats and vulnerabilities.
- Define and create controls to mitigate risks.
- Report security incidents.
- Create action plans.
- Generate reports for decision-making.
- Involve employees in risk management and achieve risk culture.
What are you waiting for? Create your free account in the Free Plan and learn more about the features of our ISMS system. Or you can also schedule a meeting with one of our experts to learn more and resolve your concerns.
You May Also Like
These Related Stories
Prioritize risk with a control matrix

Heat map: a tool to optimize risk management

8 tips to prevent cyber attacks

4 operational risk factors

5 steps to make a risk map


No Comments Yet
Let us know what you think